WordPress is an open source software, developed by a big community of developers, and with the source code open to the public, so that anyone can submit bugs, point out security issues and propose fixes. This is the beauty of open source software: Everything is transparent, anyone (that has the necessary knowledge) can assess the source code for vulnerabilities and anyone can suggest patches, real fast. That said, there is another side on this coin: Hackers (many of whom are expert programmers), can also assess the source code for vulnerabilities and bugs and exploit it. The core of WordPress is quite secure. However, there are, and have been in the past, several vulnerabilities that have been dully exploited and brought down many sites using WordPress. Also, WordPress is vulnerable cause it has an additional layer of software, on the top of the core, that can be good, or bad coded: plugins and themes. A malicious attack can take advantage of a vulnerability of an older WordPress version, of a vulnerable or insecure plugin, of a badly coded theme, etc.
Protect your website
Rather than trying to recover a hacked website, you can take some steps to better protect it from hackers. Simple steps as those outlined below will not save you from an insistent malicious person, but will help you from being a low hanging fruit:
- Always use the most recent WordPress version.
- Always keep your plugins and themes updated.
- Never use premium themes and plugins from dubious sources – buy them legally from their developers.
- Do not use an easy to guess password and do rename the main user from
adminto something less obvious. - Use a limited permissions user for content updating. You don’t need to use your
adminaccount to post a new post.
Also see our older post Is your WordPress site secure? Simple things to increase Security for some extra security tips.
Always keep a backup
Depending on how often you update your content, a daily backup might be necessary, or a weekly. Aim for at least a monthly backup. You can take a backup in two ways:
- Manually. First, you have to backup your database – this is where your posts and comments reside. You have to log in to your
MySQLdatabase viaPhpMyAdmin, choose your database (wpin this example) from the left panel and click on theExporttab on the main panel: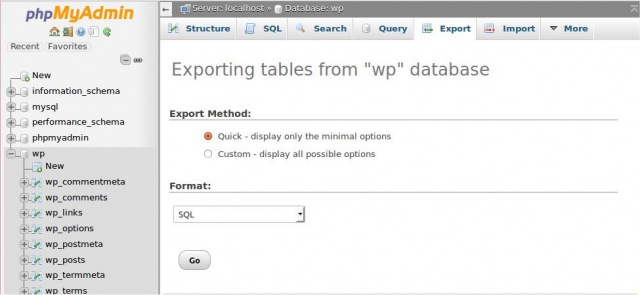 Click on “Go” and you will be prompted to download the database file. Then, you have to also backup the
Click on “Go” and you will be prompted to download the database file. Then, you have to also backup the wp-contentfolder via your FTP server. With this, you will have backed up your uploads, themes and plugins. Last, take a copy of yourwp-config.phpfile, as well as your.htaccessfile. A quick note regarding.htaccess: it is possible that you do not have this file at all, if you have never used permalinks or a plugin that writes to it. Also, as the dot.in the beginning makes it invisible in Unix servers, you might have it but not seeing it. Select the option to show hidden files on your FTP and you will be able to locate it. - With a backup plugin. To automate the backup process, you can use a backup plugin. There are many popular backup plugins, including the premium UpdraftPlus plugin, as well as VaultPress by Automattic, part of the premium add-ons for JetPack. Some great free backup plugins include:
- BackWPup

- The free version of UpdraftPlus

- Duplicator
- As well as All-in-One WP Migration, that we have talked about in a previous article.

- BackWPup
What to do if your site is hacked.
Call a professional!
Security is serious business. Cleaning up a hacked server is a complex process, long and very technical. Hackers are experts in security and a few plugins, or an article, such as this one, will not protect you from their expertise. Cleaning a hacked server or removing malware can be as simple as deleting one-two suspicious files, or as involved as to have to fully analyze your server logs, check all your files permissions, stop processes, search every file and folder for hidden malicious scripts, examining database entries and more. That said, security specialists have high fees and, for a simple blogger or small business owner, the cost can be very steep. If you read on, we will give you some simple hints on where to search and how to perform a basic site clean-up. However, especially if you are using WordPress as a professional, to promote your business, the harm of doing an inadequate malware clean up, and have your site penalized by search engines and avoided by potential customers, might be higher than paying an expert to properly clean and secure your site.
Delete your site and re-install from backup.
If you already have a good, clean backup, maybe the best solution is to completely delete your WordPress installation and restore your site from the backup.
- Connect to your site via FTP, make sure that hidden files are visible and delete everything inside the directory where WordPress lives.
 |
|---|
Here my WordPress files live in the www folder |
- Check the other top level directories on your FTP server and manually check the files for anything unusual.
- Log off your FTP server and reset your FTP password – can be done via your CPanel, or you can ask your host to reset it for you.
- Reinstall the most recent version of WordPress
- Install your backup plugin and restore your WordPress from the backup. If you took the backup manually, you will have to manually restore the database and the
wp-contentdirectory. WordPress documentation (the codex) has a very detailed article that explains how to restore your database from backup
Search and eliminate the malware scripts
If you do not have a recent, clean backup, or, for other reasons, you are not comfortable deleting all your website and restoring it, here is how you can get an idea on what’s happening to your site:
- Scan your site with Sucuri Security plugin.
 Sucuri is a very reputable security company that offers many plans to audit, secure, and clean-up your website. Additionally, it offers a WordPress plugin that can scan your site files for integrity, as well as see the activity in your website (who logged, when, from which IP). They also offer integration with their malware scanner. However, the plugin version in wordpress.org has not seen an update in 7 months. The development version of the plugin, fully patched, updated and working with WordPress
Sucuri is a very reputable security company that offers many plans to audit, secure, and clean-up your website. Additionally, it offers a WordPress plugin that can scan your site files for integrity, as well as see the activity in your website (who logged, when, from which IP). They also offer integration with their malware scanner. However, the plugin version in wordpress.org has not seen an update in 7 months. The development version of the plugin, fully patched, updated and working with WordPress 4.7.4 can be downloaded from the plugin’s GitHub page
- Remove backdoors and firewall-protect your site with Anti-Malware Security and Brute-Force Firewall
 This plugin makes use of a database of “Known Threats” and will use these definitions to scan your site and automatically remove any thread found. Also, it will block by firewall several malware from exploiting known vulnerabilities of your site.
This plugin makes use of a database of “Known Threats” and will use these definitions to scan your site and automatically remove any thread found. Also, it will block by firewall several malware from exploiting known vulnerabilities of your site.
- Manually re-examine all your files.
You can refer to the excellent, detailed article from Sucuri for a step-by-step guide on how to deal with a hacked site. Here is a bullet-point list for reference:
- Log in to your database and check for suspicious WordPress users, especially with admin permissions:
 |
|---|
The table we are looking for is called wp_users, if you haven’t changed the prefix during installation. If you don’t recognize any of the listed users, remove the record |
- Before removing a user, write down their
ID. Then remove the users as above. We have to clean up their entries in_usermetaas well, so let’s select the tablewp_usermeta, go to theSQLtab on the top and type the following query:
DELETE FROM wp_usermeta
WHERE NOT EXISTS (
SELECT * FROM wp_users
WHERE wp_usermeta.user_id = wp_users.ID
)
 To be on the safe side, run “Simulate query” first (1) and examine the records that will be deleted. If everything is correct, then run “Go” (2).
To be on the safe side, run “Simulate query” first (1) and examine the records that will be deleted. If everything is correct, then run “Go” (2).
- Delete all unused themes and plugins via your FTP.
- Check one by one all the files in
/wp-content/uploads/. Malicious scripts are often hidden there. - View your
.htaccessfile and check for any entries that seem suspicious. - If applicable, dowload your theme’s and plugin’s settings, delete them from FTP and then re-upload a fresh version from the
wordpress.orgrepository or from the download provided by your premium theme or plugin vendor. - Scan again! with one of the plugins mentioned above.
We hope this article provided some useful information. We would like to stress, again, that webserver, database and website security is a very serious matter. A hacker who specifically wants to target your website (as opposed to a hacker sending automated scripts to target vulnerable, not-secure websites), will be more than capable to bypass all the above steps. The best and most permanent solution to secure your website is to hire a professional to do it for you.
 Click on “Go” and you will be prompted to download the database file. Then, you have to also backup the
Click on “Go” and you will be prompted to download the database file. Then, you have to also backup the 



